Even though you don't see security and bleeding edge release candidates in the same sentence every day, you need to secure your API's.
I have been using Auth0 as my identity provider for a recent project, and they have AMAZING documentation that include everything you need, including complete code examples in step by step instructions. Check it out here, they have really put some work into making it super easy to use.
They support most popular frameworks for apps, web, and backend, but so far they do not have a separate choice for a ASP.NET core backend. "ASP.NET Web Api (OWIN)" is close, but not quite right.
Although it's not in the documentation yet, Auth0 have created an example for RC1 on github, but I still went through some struggles worth mentioning while putting the pieces together!
TL;DR:
When using ASP.NET Core 1.0 RC1 you will have to use RS256 as the signature algorithm.
The JWT signature algorithms
Auth0 supports HS256 and RS256 as signing algorithms for your JWT. The default is HS256, simply signing the token with your client secret. You can change this in your application settings, by clicking "Show advanced settings", and opening the OAuth tab:
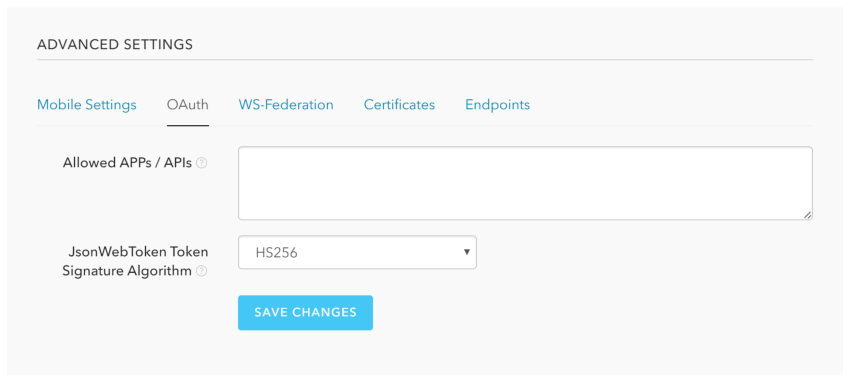
HS256 was fine for my use. The problem was that the example on github was for RS256. I decided to try anyway, as it should be pretty simple to set up.
Can I Use HS256?
I got my settings from Auth0 and created some app settings:
I then implemented the use of JWT bearer tokens using the example from Auth0, but modified it into the following code, using a SymmetricSecurityKey for HS256:
At first I was unable to get anything else than a 401 on my API calls, and nothing helpfull in the log, but it turns out a very central part of the setup was to set the AutomaticAuthenticate option to true to get the authentication running. Maybe a no-brainer, but it was not included in the Auth0-example.
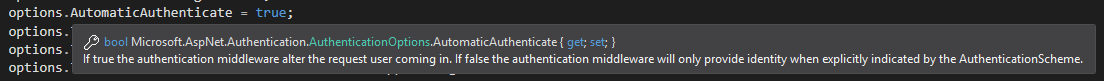
The result of this was simply the following exception on running the API:
IDX10640: Algorithm is not supported: 'HS256'
It seems this will be supported in RC2, but nightly builds and security simply does not belong together, so I gave up on HS256, and moved on to RS256.
Can I Use RS256?
Knowing that HS256 was out of the question, I wanted to simplify the setup of RS256 as much as possible. To avoid including certificate files with my deploy, I decided to put the public key from Auth0 in my app settings.
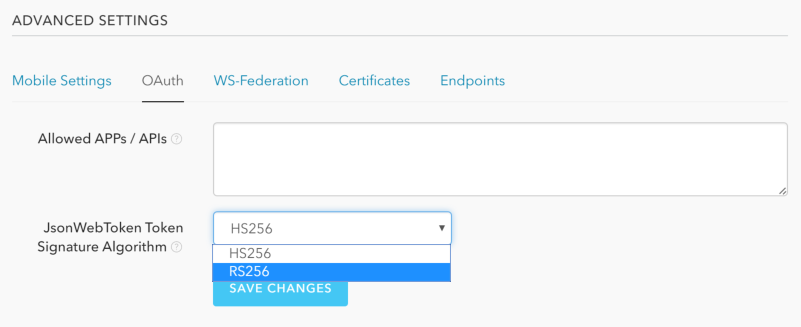
First, change the signature algorithm to RS256:
Then you need to get the public key from the certificate, go to the "Certificates" tab and copy the content of the signing certificate:
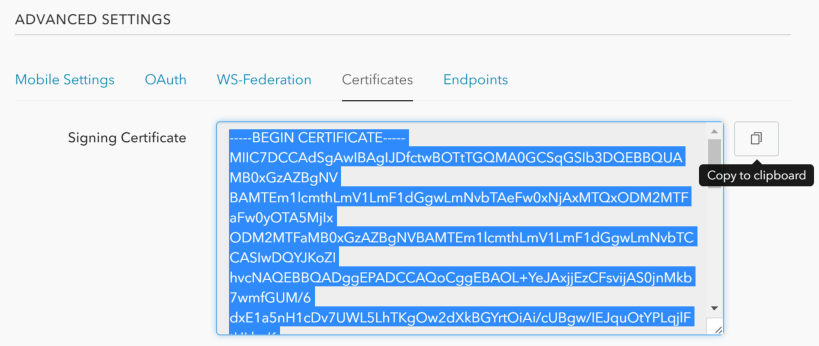
(this is just the public key)
To keep this in my settings I flattened the content by removing "-----BEGIN CERTIFICATE-----", "-----END CERTIFICATE-----", and all the line breaks. Then I could simply convert the string into a byte array and create the X509Certificate2 instance I needed from the bytes.
The following code validates the token signature using RS256:
This works perfectly, and now I just needed to secure my controller actions with the Authorize attribute:
Voila!

